Firewalls and ArcGIS Server
Firewalls and ArcGIS Server |
|
| Release 9.3 |
|
Every computer has thousands of ports through which other computers can send information. A firewall is a security mechanism that limits the number of ports on your machine through which other computers can communicate. When you use a firewall to restrict communication to a small number of ports, you can closely monitor those ports to prevent an attack. Also, you can configure the firewall to restrict communication to a port known only to you.
Firewalls can be implemented through hardware, software, or a combination of both. Firewalls work best in detecting attacks that could enter or leave your system through an open port, such as worms and some Trojan horses. They do not protect you from viruses attached to e-mails or from threats inside your network. Therefore, although firewalls are important, they should not be the only component of your overall security strategy. Anti-virus software and solid authentication and authorization techniques are examples of other security strategies that should be deployed in conjunction with firewalls.
ESRI does not recommend or support firewalls between ArcGIS Server components. This includes firewalls between the Web ADF and the GIS Server as well as firewalls between the server object manager (SOM) and the server object container (SOC). The recommended technique for protecting an ArcGIS Server system with firewalls is to configure a reverse proxy Web server within a perimeter network (also known as a demilitarized zone (DMZ) or screened subnet). In this scenario, the reverse proxy Web server receives incoming HTTP requests through a firewall that restricts traffic to a known port (usually port 80). It then sends the request through another firewall--using a port unknown to the end user--to the ADF Web server in a secure internal network. The ADF Web server is then free to establish unrestricted DCOM communications with the other ArcGIS Server components. In this way, the entire GIS server operates within a secure internal network and does not require firewalls between its components.
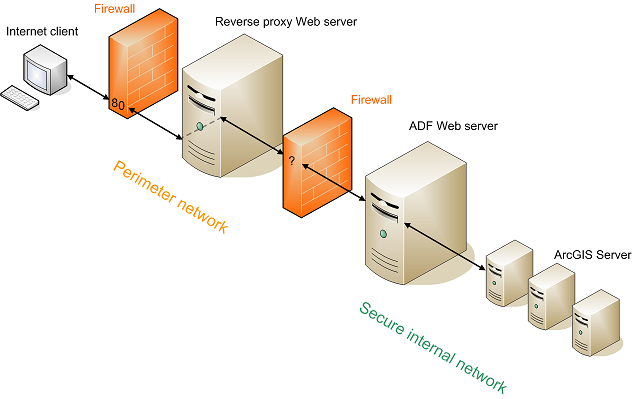
Here's a closer look at each component in this scenario:
ESRI Knowledge Base article 32634 describes a procedure for configuring ArcGIS Server for the Microsoft® .NET Framework to work with a reverse proxy Web server.