Security Concepts
Security Concepts |
|
| Release 9.3.1 |
|
ArcGIS Server at 9.3 introduces Role based Access Control (RBAC) to secure the capabilities published by the GIS Server. To administer and develop with this security model, it is very important to understand the various components that make up the security model and how these components interact with each other. Some of the components that we have introduced are the Principal and Permission Stores, Token Service, Secured Web Services and Secured Web Applications.
The documenation on Security is divided into differnt topics. Each topic begins with an overview of a component and then it goes on to explain the specific workflow.
This section will give you a conceptual overview of the various components that form the Security functionality at 9.3 and how they fit into the security model.
The picture below gives a diagrammatic representation of the various components of the security model.
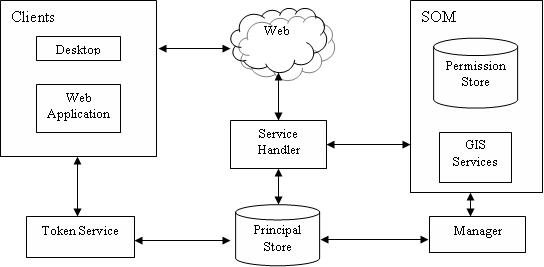
The Principal Store is a repository of web users and roles. It holds the information about users who wish to consume the services published by the ArcGIS Server over the web. As the ArcGIS Server security model is based on a role based access control, the GIS administrator will assign certain privileges to each of the roles (for example: a role 'Planner' can access a certain GIS services) and assign these roles to the users. Each user will then inherit all the permissions of all the roles that have been assigned to him.
ArcGIS Server can work with a variety of stores to maintain and access user and role information. You can use a relational database server (for example: Microsoft's SQL Server or MySQL etc) or a directory server (for example: LDAP or Microsoft's Active Directory). You can also configure the Server to access this information from a proprietary store by writing extensions (using the principal store API) and then setting it up so that Manager will connect to your proprietary store through your extension.
The Token Service will connect to the configured Principal Store for user authentication. The service handlers (for example: REST and SOAP handlers) will also look up the Principal Store for role information associated with a requesting user. Using Manager, you can manage user and role information in your stores.
For more information on how to configure and use the Principal Store, see the 'Configuring Security' topic in the documentation.
For more information on how to write extensions using the Principal Store API, see the 'Extending the Princiapl Store' topic in the documentation.
The Permission Store is a repository of privileges that have been assigned to the roles. It stores information regarding the list of GIS Services that are accessible to a particular role.
The Permission Store is maintained by the Server Object Manager (SOM). You don't have to explicitly configure and maintain it. The Permission Store also exposes an API with which to access it.
For more information on how to setup permissions on your GIS Serivces and Web Applications, see the 'Security for Web Services' and 'Security for Web Applications' topics in the documentation.
When the GIS Server has secured its published web resources, any web client who wishes to consume these resources must provide a valid credential while accessing the resource. At 9.3, ArcGIS Server will support two different authentication schemes to validate the user credential.
Web clients must provide a token when they want to access a GIS Service that has been secured using the ArcGIS Managed Authentication. Tokens can be acquired from a token service installed by the ArcGIS Server. Each token is an identity for the user. The service handlers are updated to process this token and authenticate the client user.
Clients like ArcCatalog or web applications built using the Manager are capable of seamlessly consuming GIS Services that have secured using ArcGIS Managed Authentication. You don't need to explicitly get tokens from a Token Service when working with these clients.
This is a new authentication mechanism in the ArcGIS Server at 9.3 and JavaScript clients powered by the REST API (also new at 9.3) can seamlessly consume secured services.
For more information on working with tokens, see the 'Token Service' topic in the documentation.
Web clients attempting to consume a GIS Service that has been secured using Java EE Container Managed Authentication will be challenged by the web container to provide authentication credentials.
Here, the service handlers (for example: REST and SOAP handlers) are secured by the web container in which they are deployed. Most web containers support different authentications schemes such as BASIC, DIGEST or Client Certificates etc.
A Web Application that has been secured using this authentication mechanism will display an HTML login page when you attempt to access this application. Once you have entered your credentials, the login control will validate the information provided with the user credentials in the Principal Store that has been configured for the application. You will be granted access to this application only if you belong to a role that has been given permission to access this application by the GIS administrator.
For more information on how to secure Web Applications, see the Security for Web Applications topic in the documentation.
In this case, the Web container in which the application is deployed will challenge the you for your credentials. The container then in turn will authenticate your credentials with the user information in its configured realm and authorize your access.
You need to explicitly setup your Web container with an appropriate realm that would contain user and role information.
For more information on how to secure Web Applications, see the Security for Web Applications topic in the documentation.
In order to seamlessly support scripting clients, ArcGIS Server at 9.3 has introduced a token based access to secured GIS services. Tokens encapsulate the identity of a particular requesting principal (user) and are granted by a Token Service that is installed as a part of the ArcGIS Server.
The Token Service will communicate with the configured Principal Store to authenticate in coming requests for tokens. The GIS Server is capable of deciphering these tokens and granting role based access to requesting resources.
Token Service is a part of the ArcGIS managed authentication for securing GIS Services.
Tokens can be requested by using the URL or by using the GUI (web page). JavaScript application developers need to fetch a token and use it in their applications that are consuming a secured GIS service.
For more information on working with tokens, see the 'Token Service' topic in the documentation.
GIS Web Services are secured using a role based access control mechanism. You can set permissions on services using Manager. When security is enabled on the GIS Server only those users belonging to roles that have permissions to access the GIS services will be granted access.
To secure your GIS Web Services, you have a choice of authentication schemes between the ArcGIS Managed Authentication based on Tokens and the Java EE Container Managed Authentication (described above).
For more information on how to secure web services, see the 'Securing Web Services' topic in the documenation.
Web applications created in Manger can be secured by using the ArcGIS Managed Authentication or by using Java EE Container Managed Authentication (described above).
You can assign a particular set of roles, permissions to access the Web Application. Users belonging to only these roles will be allowed access to the application.
For more information on how to secure web applications, please see the 'Securing Web Applications' topic in the documenation.