Securing local connections to services
Securing local connections to services |
|
| Release 9.3 |
|
Local connections to a GIS server--and the services running on it--are managed by the operating system of the server object manager (SOM) machine. In much the same way the operating system allows you to create and delete files on your own computer, yet prevents you from doing so on your colleague's computer, the operating system on the SOM grants some users access to the services running on the server machines, while denying access to others. When you log in to your computer, the user name and password you specify identify you as a valid user on your network. Based on your operating system account, you are allowed to perform a certain set of actions--one of which might be to access a GIS server.
Before you can begin to use your GIS server, you need to establish who can access it. Once you've done that, you'll be able to connect to your GIS server and add services to it.
To whom should you grant local access to your GIS server? The answer to this question will depend on what kind of services you run on your server and how you plan to use them. In some cases, the services you place on your server should be made available to everyone. In other cases, you might want to restrict access because a service contains sensitive information that only certain individuals should see.
As the administrator of the GIS server, you allow people local access to the GIS server by adding their operating system account to the list of users who should have access to the server. In reality, there are actually two lists: a list of users who can use the services running on the server and a list of users who can administer the server itself (that is, add, delete, and modify server services). Because it is the operating system that ultimately controls access to the server, you use two operating system user groups--ArcGIS Server users and ArcGIS Server administrators--to manage the two lists of users. A user group simply defines the set of users who have access to a particular resource, in this case, a GIS server.
In general, the list of accounts you add to the ArcGIS Server user and administrator groups will depend on what clients you anticipate will connect to the server. Each operating system account from which ArcGIS Desktop is run will need to be added to the ArcGIS Server users group if you want that client to access the GIS server. Additionally, each Web application you create can connect to the GIS server through a particular operating system account. Each account your Web applications utilize should be added to the ArcGIS Server users group as well.
You do not need to add the SOM and SOC accounts to the administrator or user groups. These accounts are only used by the operating system to start and stop processes on the GIS server.
When you install ArcGIS Server, the installation automatically creates the ArcGIS Server users (agsusers) and administrators (agsadmin) groups for you. These are created as local operating system groups on the SOM machine and on each container machine. The ArcGIS Server installation doesn't automatically add any users to these groups for you. Thus, you will need to add users to these groups, depending on the type of access each user should have. Of course, the first account you'll need to add to the agsadmin group is your own.
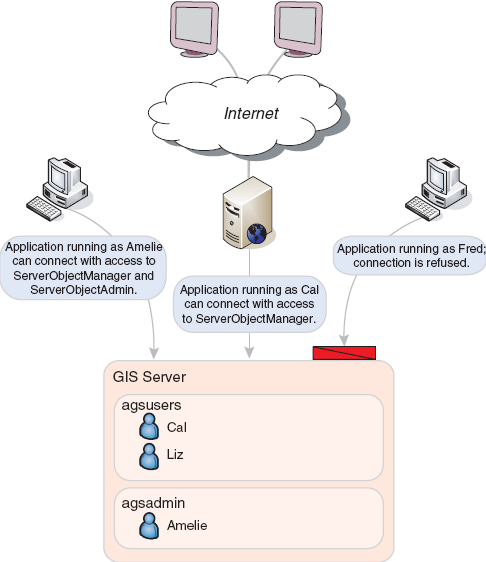
When applications make local connections to the GIS server, they are authenticated against the agsusers and agsadmin groups on the GIS server.
How you choose to add user accounts to these groups depends on how your organization manages users in general. If your organization has a number of user groups already established, you might choose to add particular groups as members of the agsadmin and agsusers groups. By allocating users based on other groups, you can minimize the amount of work you need to do to change access to your GIS server. For example, if a new employee is hired and added to one of your organization's existing groups, access to your GIS server will automatically be granted because the employee is a member of a group that is a member of the ArcGIS Server users group. Alternatively, you can add individual users to the agsadmin or agsusers groups.
Members of the ArcGIS Server users group (agsusers) have consumer-level privileges on the GIS server. Consumers can view and access services; however, they cannot perform administrative tasks, such as add, remove, or modify preconfigured services. They also cannot modify properties of the server itself, such as adding and removing machines.
Members of the ArcGIS Server administrators group (agsadmin) are granted access and administrator privileges on the GIS server. Connecting as a member of the administrator group allows you to
A desktop client application to ArcGIS Server will run as the user account that started the application. For example, if you are logged in to a desktop computer as the domain user ANDY on the domain AVWORLD and you are running an application such as ArcCatalog, the identity of the application is AVWORLD\ANDY. When you make an ArcGIS Server local connection in that ArcCatalog session, you are connecting as AVWORLD\ANDY. As long as AVWORLD\ANDY is a member of agsusers on the SOM, you will be able to connect. If AVWORLD\ANDY is a member of agsadmin, you will have administrator privileges on the server through that connection.
In general, it's good practice to use an account with more restrictive permissions when performing your daily tasks and to use the administrative account only when you need to administer your server. In Windows, you can use the runas command to connect to ArcCatalog with an operating system account other than your current login. You can run the runas command at the command prompt and, in some operating system versions, as a context menu option on the ArcCatalog executable file located in the bin folder of your installation location. For example, at the command prompt, type the following:
runas /user:username "C:\Program Files\ArcGIS\bin\ArcCatalog.exe"
Alternatively, navigate to the ArcCatalog.exe file in the bin folder or locate your shortcut to it, right-click the executable file, then click Run as. Consult the Windows documentation for more information on using the runas command.
When you are using the Web Application Developer Framework (ADF) to build Web applications that access local services, you will need to specify an identity. The account that you use for the identity must belong to either the agsadmin or agsusers group on each local server to which your application will connect. When end users access the application, they will not have to enter a name and password to access the service. Instead, the identity will be used. The encrypted identity information is stored in the application's web.config file.
Restricting access to some services but not others on the same GIS server is only available through Internet connections. See the section Securing Internet connections and Web applications to learn how to implement this.