Ways to implement security in ArcGIS Server
Ways to implement security in ArcGIS Server |
|
| Release 9.3 |
|
Your GIS server represents an investment of effort and resources that you want to protect. ArcGIS Server contains security mechanisms that can prevent unauthorized users from accessing your services and applications. You can also use ArcGIS Server to configure tiers of access for different groups within your organization.
There are several aspects of your GIS server that you can secure:
Securing your system as a whole
Securing your system as a whole involves protecting your hardware and software and configuring ArcGIS Server to work within your organization's existing security infrastructure. Your organization probably uses a firewall to protect the internal network from malicious Internet users. Your ArcGIS Server system, sitting behind a firewall, does not require that individual firewalls be placed between its components.
The GIS server uses operating system accounts to access the data that it needs. You need to grant these accounts permission to access your data, but it's also a good practice to avoid granting them other permissions. This section of the help provides guidelines for configuring these accounts.
Finally, whenever users send sensitive information to your server, such as when logging in to Manager, it's recommended that you use a Secure Sockets Layer (SSL) connection. SSL encrypts the data, protecting user names and passwords from those who would maliciously intercept the transaction.
Securing local connections
Local connections to the GIS server are handled through operating system users and groups. Two groups, agsadmin and agsusers, are created by the installation process and are allowed access to the GIS server. You need to add to these groups any user that will make local connections to the GIS server.
Securing Internet connections (Web services)
You can configure security for ArcGIS Server Internet connections (Web services) through the Manager application. This includes defining users and roles and determining which privileges roles should have for working with the services.
Securing Web applications
You can use Manager to define which users and roles can access your Web applications and what level of privileges they should have.
You can think of ArcGIS Server security in terms of two "zones", shown in the graphic below. This section of the help contains books that correspond to the zones.
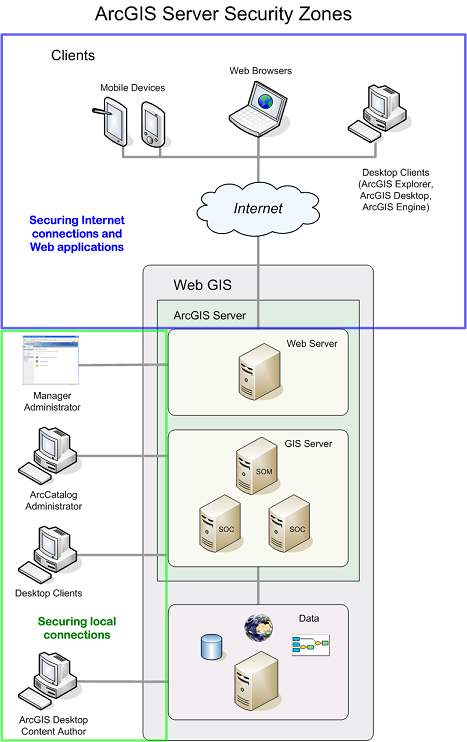
All GIS server administrators need to be concerned with the local security zone because administering the server requires an account that has been added to the agsadmin group. You can immediately start configuring local security by adding or omitting users from the agsadmin and agsusers groups. In contrast, Internet security requires that you do some preparatory work of configuring a user and role store and explicitly enabling security before you can prevent users from accessing your Web applications and services.
The users of your GIS server will determine where you focus your security strategy. If you have a Web application or service that exposes various levels of access to anyone with an Internet connection (for example, Guest, Employee, Administrator), you need to be concerned with the Internet security zone, namely, setting up users and roles and a way of storing these. In contrast, if you have a set of services that only users on the local network will be adding to ArcMap, you only need to be concerned with the local security zone, configuring the agsadmin and agsusers groups.
Some applications require attention to both zones, such as a Web application used by employees on your LAN for editing GIS data. The application needs to run as a member of the agsusers group, involving the local security zone. At the same time, access to the application needs to be managed through users and roles, involving the Internet security zone.