Securing Web Services
Securing Web Services |
|
| Release 9.3 |
|
When web services are secured, clients requesting access to these web services must provide credentials of user who belongs to at least one role that has been granted access to that particular web service.
You can administer permissions (allow certain roles to access) on folders or web services created on the ArcGIS Server through Manager.
Folder level permissions are a convenient way to toggle the permissions on all the resources (folders and services) contained in the folder.
The screenshot below shows the diaglog for applying permissions on a folder.
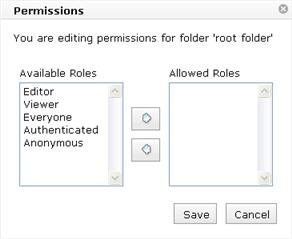
You can set permissions on a folder by going to the Services panel in the Manager, and selecting the particular folder in the drop down list on the top of the page and clicking the 'Edit Folder Permissions' button. A dialog box will pop up that will list all the roles that have permission to access the folder along with a list of all the available roles (who currently don't have permissions) who can be granted permission to access the folder. Click the 'Save' button to persist the settings.
When a certain role is allowed access to a folder, all resources within the folder will be accessible to this role and vice versa. The implications of this rule is that, if a role is explicitly allowed access to a service within a folder and later on if the same role is allowed access to the folder (in which the service resides) then the role is able to access the service because of an implicit allow rule (because the parent folder is allowing access to the role). Further if the role is denied access on the folder, the role will be denied access on the service as well.
For example: Consider the following resource tree
Let us walk through how the permissions get inherited.
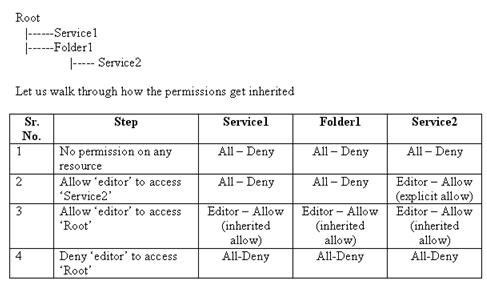
Permissions on services follow the continuous inheritance model. A service will inherit permissions from its parent folders when it is created and continue to do so unless explicit permissions are set on it. The administrator can explicitly set different permissions on the service in which case the service will break its inheritance.
You can set permissions on a service by going to the Services panel in the Manager, selecting the particular service listed on the page and clicking the 'Service Permissions' button. A dialog box will pop up that will list all the roles that currently have permission to access the service along with a list of all the available roles (who currently don't have permissions) that can be granted permissions to access the service. On clicking the 'Save' button; the permissions view is persisted into the system.
Permissions for a folder are inherited by services within the folder. For example, if you allow the role Administrators access to a folder, all services within the folder will also have this role allowed. The permissions dialog will show the role, along with other roles that you have added, if any. Folders also inherit permissions from the server root folder.
You can remove roles that a service inherits from a folder. To do so, open the permissions dialog for the service, select the role, and click Remove. This will cause that role to not be permitted access to the service. Note that users may be assigned to multiple roles, so that access must be carefully considered based on role membership.
If permissions for a folder are edited, any changes to role permissions are reapplied to all services within the folder. Note that this will overwrite any changes made to those roles for individual services. If you remove a role from the permitted list for the folder, that role will no longer be permitted access to any services within the folder. Similarly, if you add a role to the folder's permissions list, it will be allowed access to all services in the folder.
Overwriting permissions in child folders and services
When setting permissions for folders, you may see this message when you click Save:
One or more of the roles you are changing permissions for already has a permission setting in one or more services or folders inside this folder. If you continue, the permissions settings for these roles in child services or folders will be inherited. Do you want to save these changes?
This message means that you are adding or removing a role that already had explicit permissions in one or more services within the folder, or in a child folder if editing permissions of the root folder. If you proceed, all rules that role in child folders and services will be removed, and the child folders and services will inherit permissions for that role from the folder.
For permission changes on the root, the message may warn of a more significant change. For example:
If you receive this warning when editing permission of the root folder, and are not certain of how the changes will affect access to services, you should click Cancel to the warning message and examine permissions of child folders and services. You may need to follow up the application of the permissions change by then re-applying rules to child folders and services in order to produce the desired security configuration.
If you have added or removed more than one role while editing permissions, the message may mean that multiple roles are affected. You may want to examine the permissions on child folders and services to ensure that you are not overwriting permissions you actually wanted to persist.